Track vendor performance
Develop a centralized vendor repository to store critical information on each vendor relating to contracts, costs, SLAs, and KPIs, enabling continuous monitoring of supplier performance against key metrics.

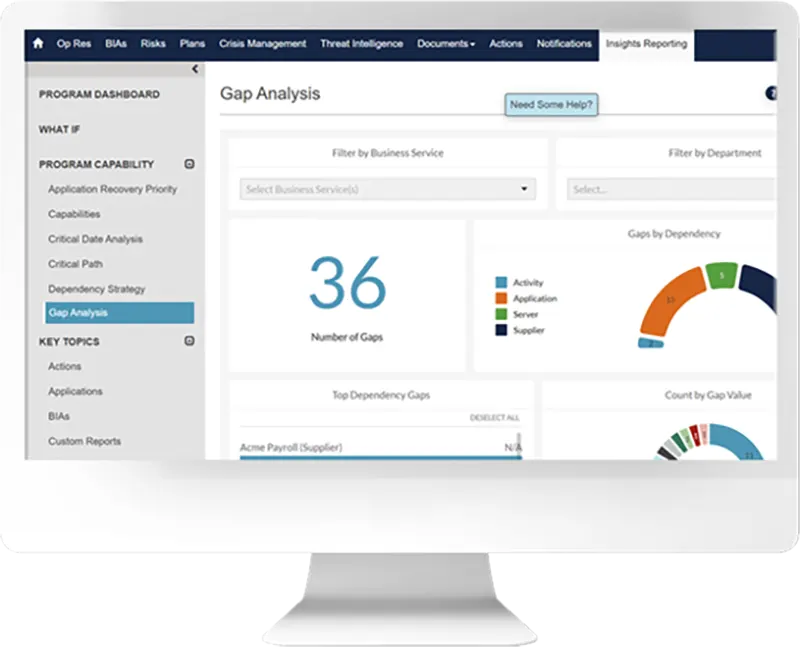
Streamline vendor risk assessments
Vendors can easily complete risk assessments, surveys, and questionnaires via an online vendor portal, workflows send reminders and chase overdue actions.

Collect third-party risk insights
Link Riskonnect’s vendor risk management software with your preferred risk intelligence provider through API integrations to get detailed insights on potential problems relating to your suppliers.
How does vendor risk management software work?
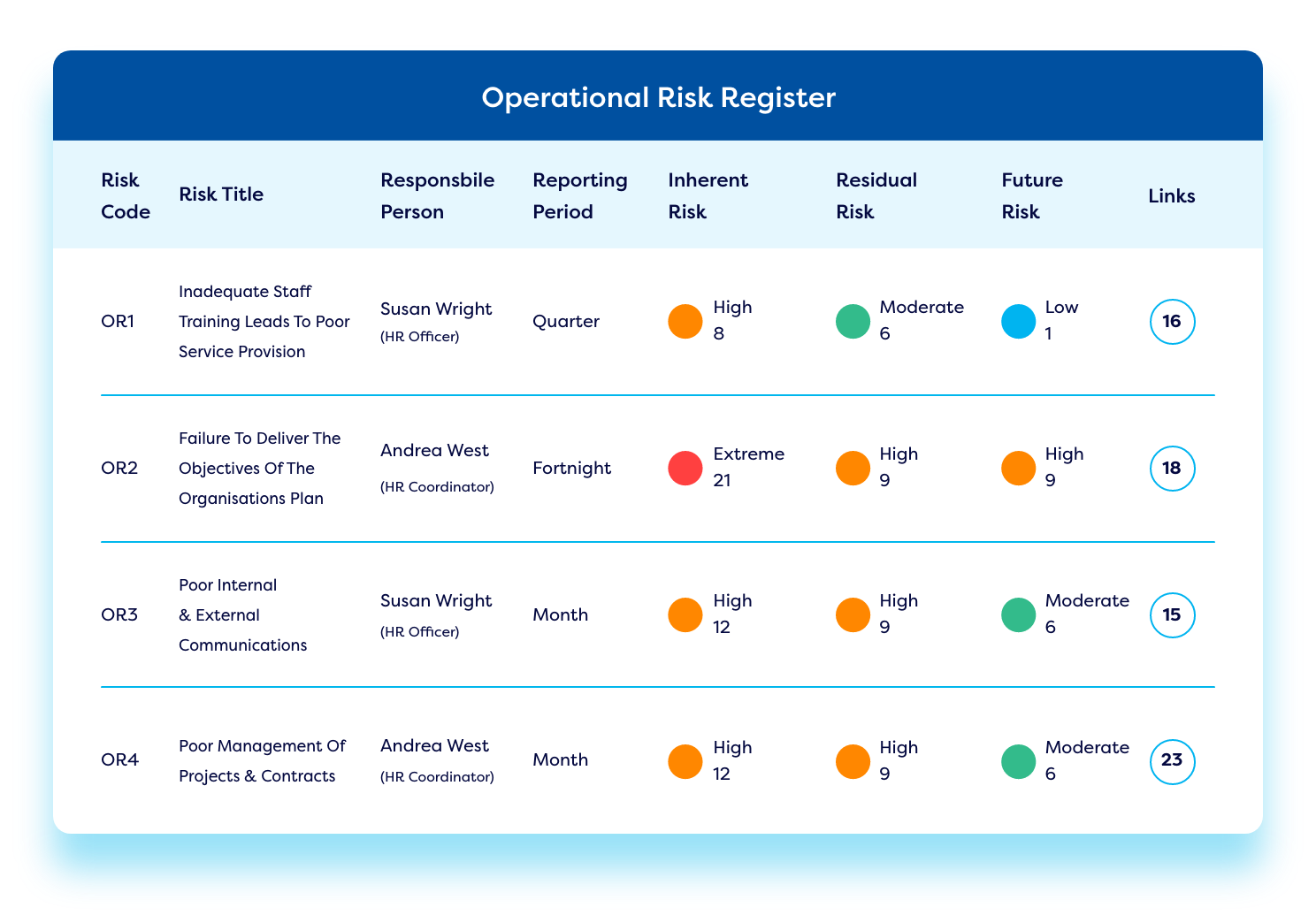
Establish a vendor register.
Build a vendor risk register to capture essential details for each supplier, including costs, contracts, key contacts, service level agreements (SLAs), and key performance indicators (KPIs) to create a centralized third-party inventory and monitor vendor risk exposure.
Automate vendor risk assessments.
Riskonnect’s vendor risk management software fully automates the vendor risk assessment process. Workflows send notifications when assessments are due, and suppliers and staff complete the details via online forms that feed into the platform. You can customize forms for different supplier categories and capture score-carding, benchmarking, and performance ratings for each supplier.
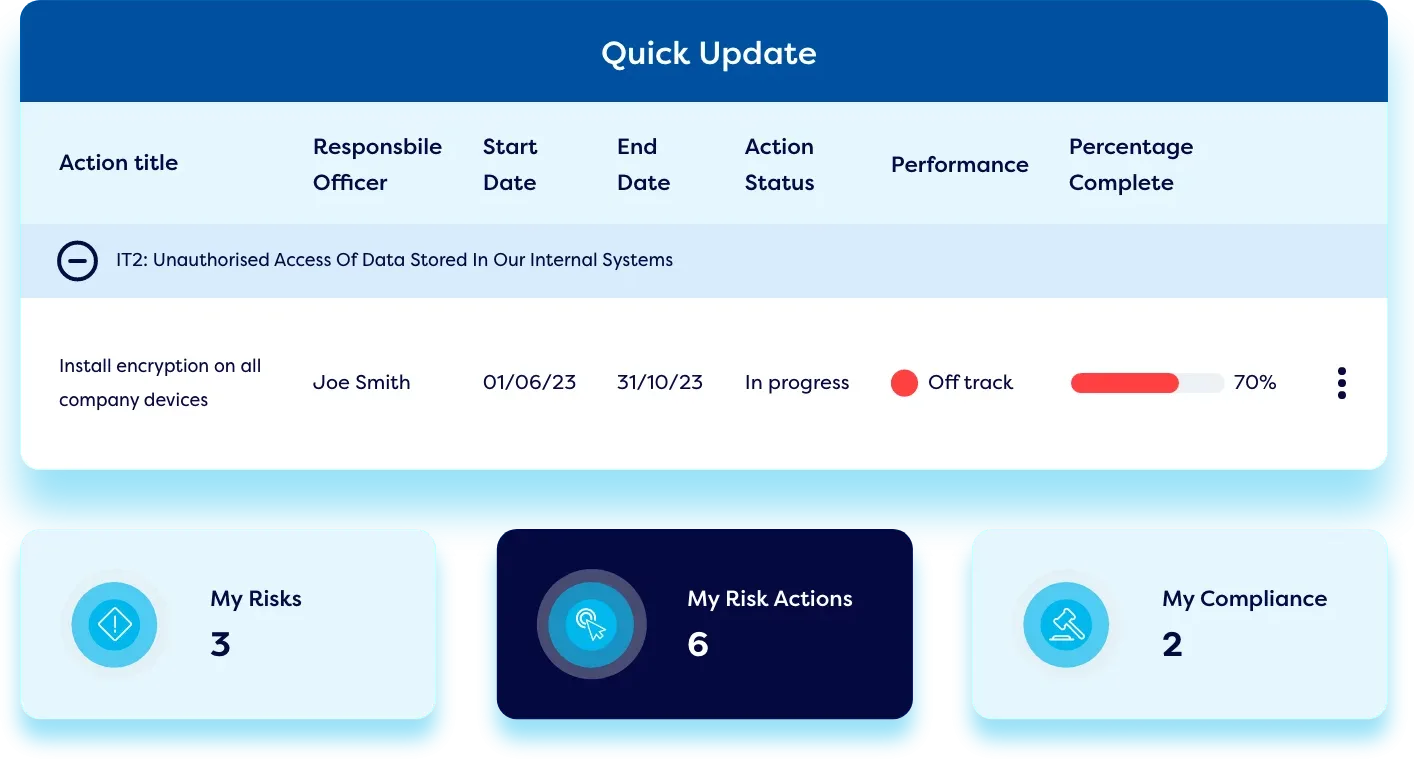
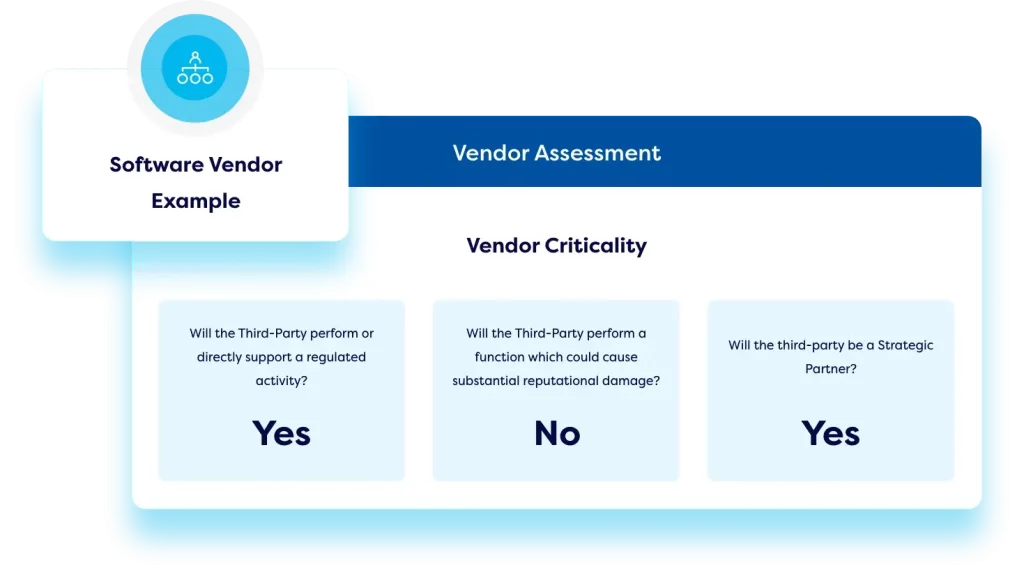
Conduct vendor reviews and questionnaires.
Design detailed questionnaires and surveys in our vendor risk assessment software to assess key vendors and use workflows to automate approvals, sign-offs, and reporting outputs. Workflow automation also facilitates regular vendor reviews and tracks the progress of corrective actions.
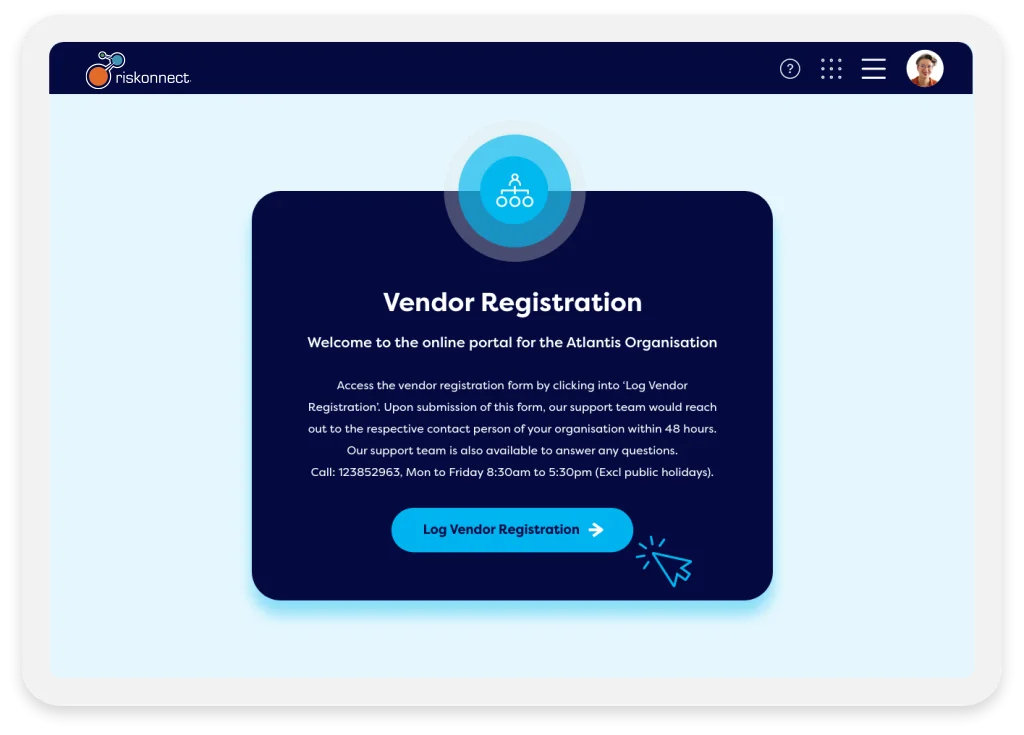
Build an online vendor portal.
Riskonnect’s third-party risk management software enables you to build an online vendor portal to consolidate vendor responses centrally. Vendors complete risk assessments, questionnaires, and surveys and upload supporting evidence via the online portal. Completed assessments automatically trigger alerts and initiate subsequent steps for internal teams.
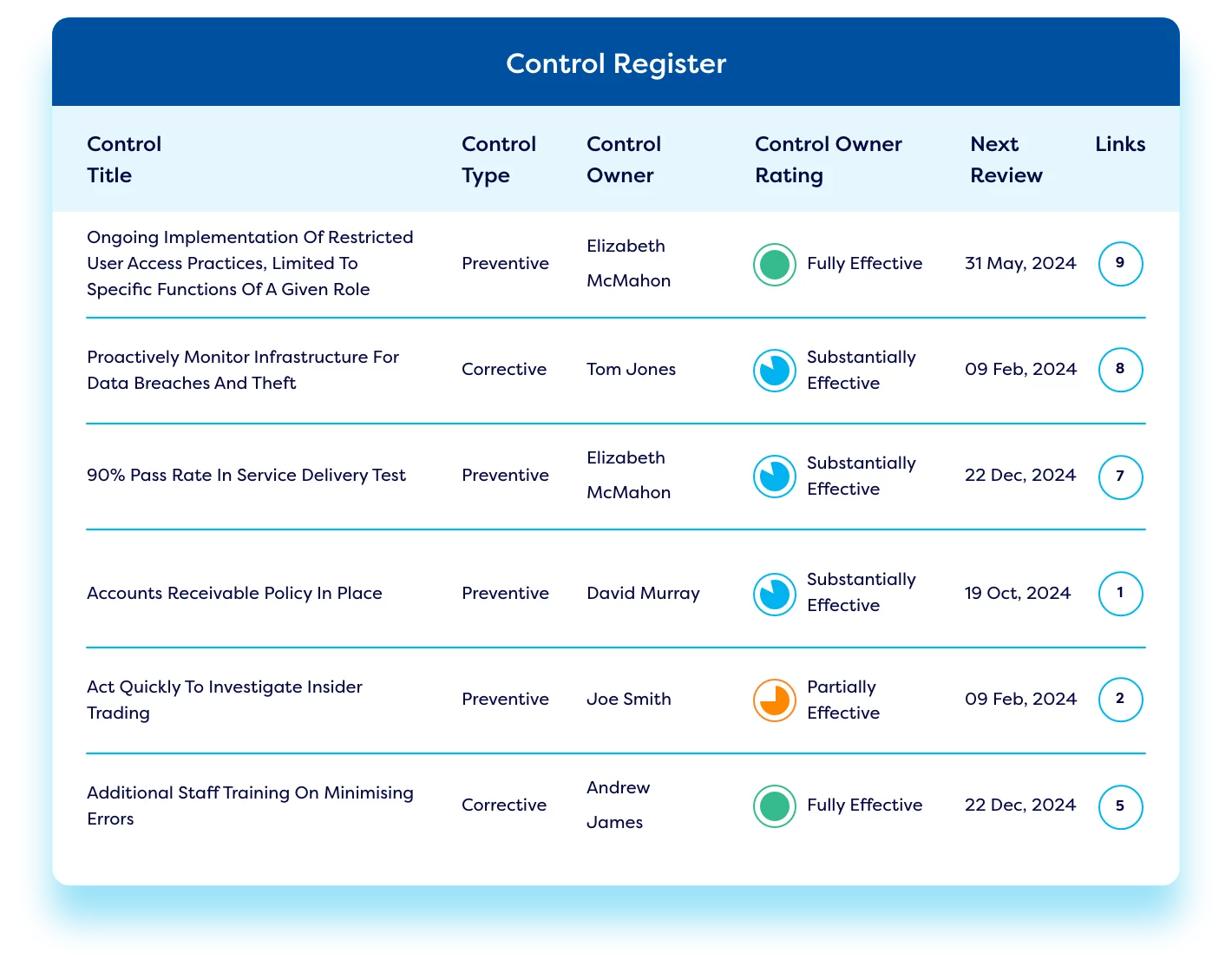
Implement controls to mitigate risk.
Establish an online control library to implement measures that mitigate vendor risks effectively and conduct regular control checks and testing. Setting robust controls protects your organization from reputational damage caused by poorly performing vendors.
Monitor supplier performance.
Monitor risk exposure by integrating APIs with other systems and data sources to track vendor performance against agreed-upon SLAs and KPIs. When risk exceeds tolerance levels or performance drops, automated workflows send notifications and facilitate the capture of any remediation actions, enabling prompt action on any underperforming service providers.
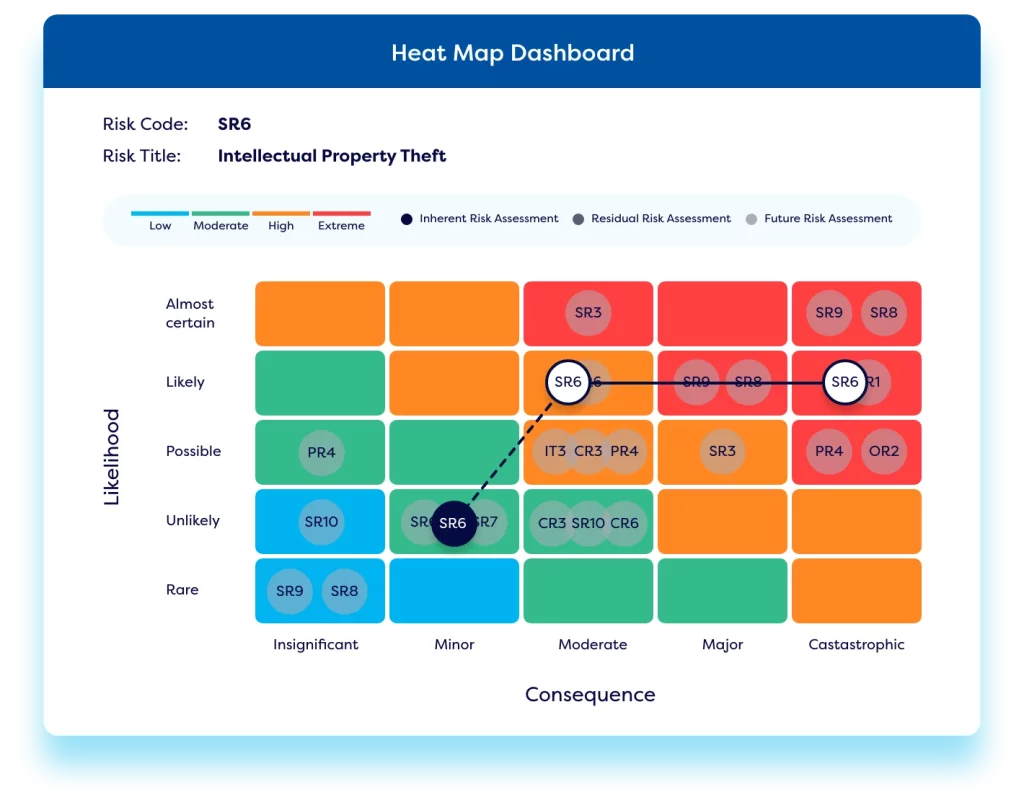

Receive third-party risk intelligence.
Get real-time data on the ethical practices, financial health, security posture, legal and regulatory compliance issues, and cybersecurity and data privacy threats relating to your suppliers by subscribing to third party risk intelligence that feeds into your TPRM program via API integrations.
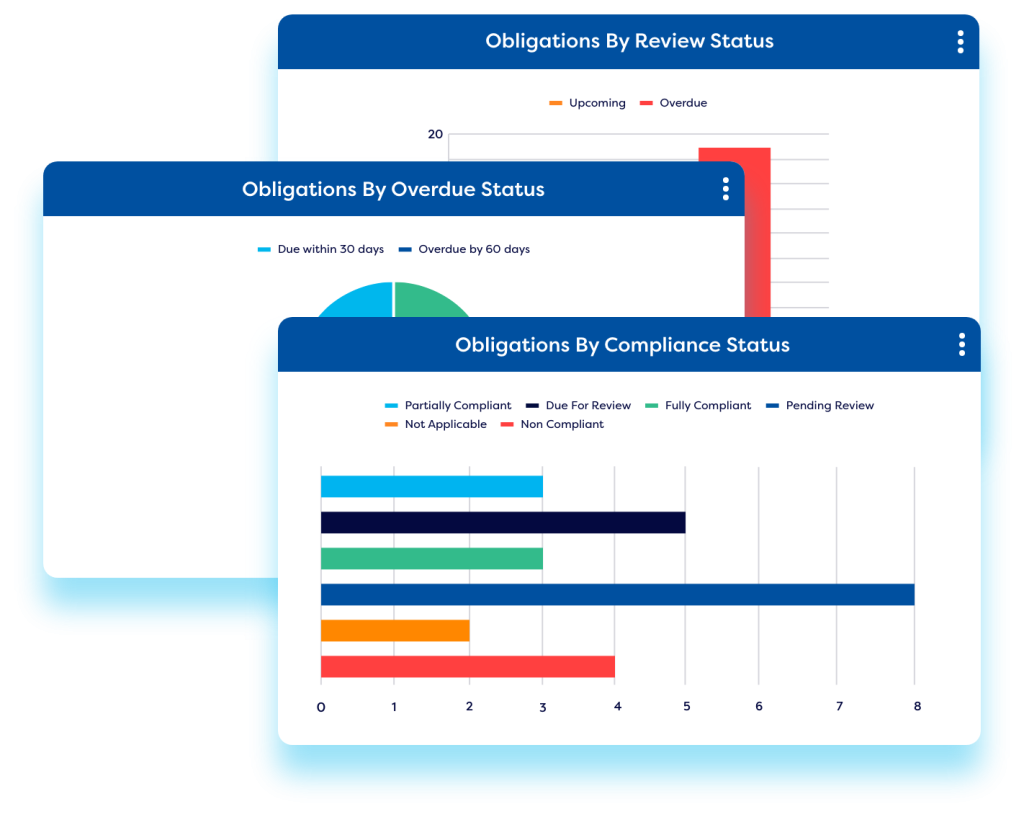
Ensure vendors comply with regulations and standards.
Feel confident that your vendors and suppliers are adhering to all applicable regulations and industry standards with our vendor compliance management software. Easily incorporate compliance requirements into vendor assessments, ensuring seamless and transparent compliance tracking during supplier audits.
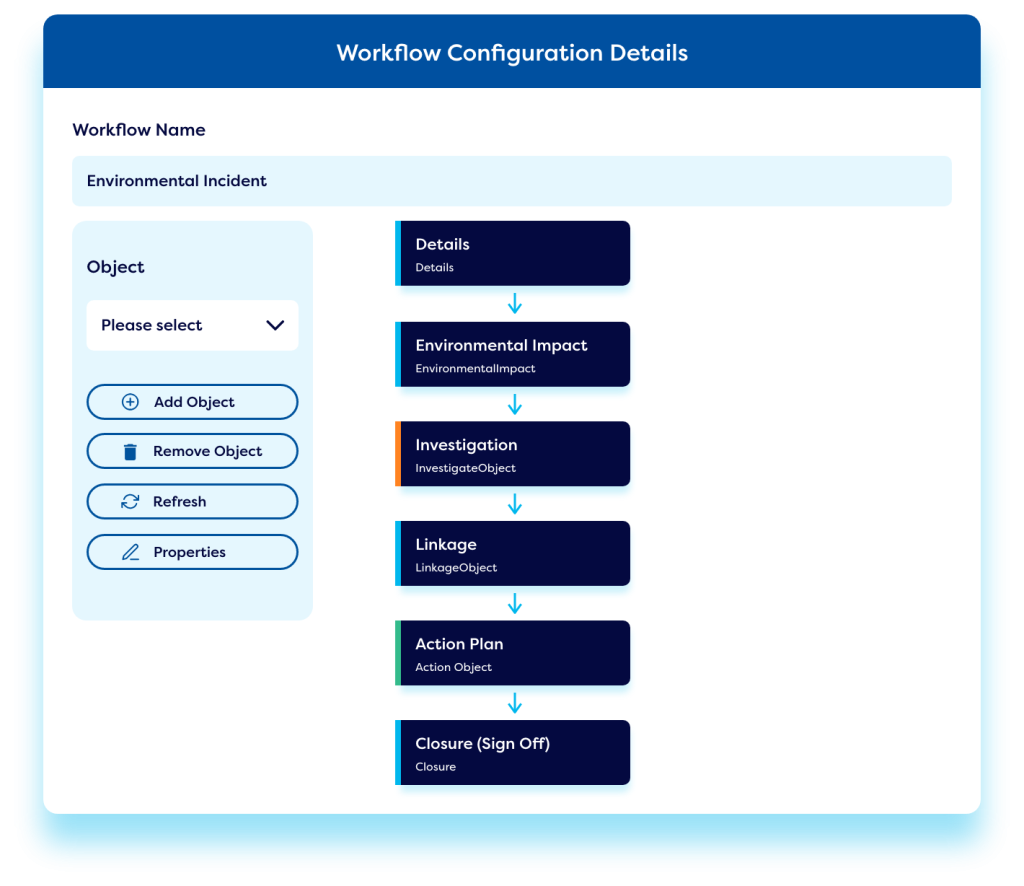
Formalize vendor onboarding and offboarding.
Structure a best-practice onboarding and offboarding process to facilitate comprehensive and consistent supplier due diligence and ensure there are no unexpected contract clauses that keep you tied into vendor relationships.
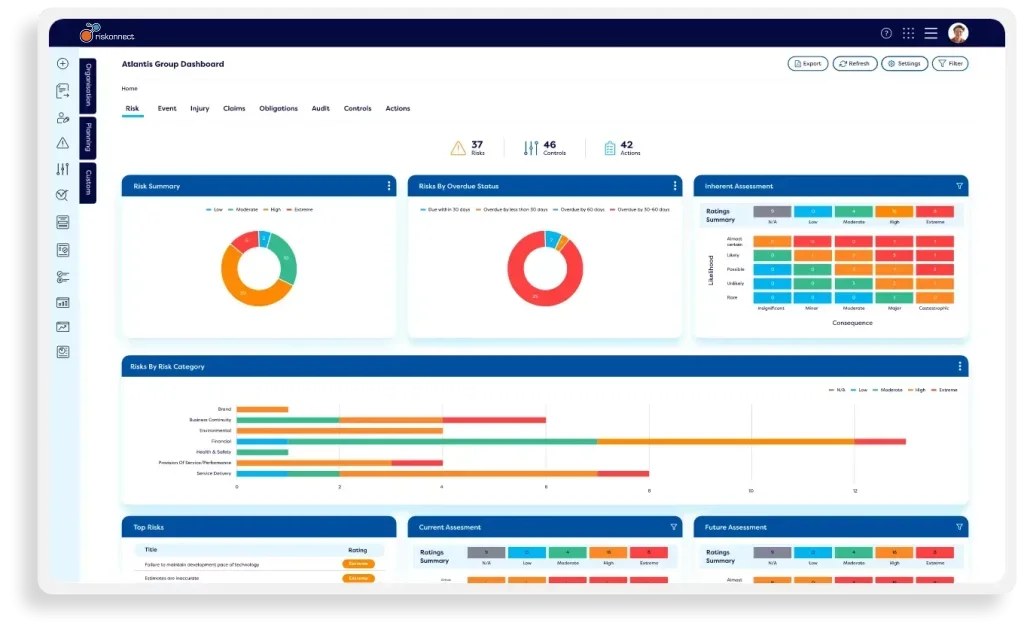
View real-time dashboards and reports.
Riskonnect’s vendor risk management solution enables you to generate comprehensive vendor risk reports on supplier-related risk to support the vendor selection process. Easily report on performance against KPIs, SLAs, and industry benchmarks to build a holistic view of third-party risk.
How can Riskonnect help?
Riskonnect is a highly configurable vendor risk management platform that can be tailored to your bespoke needs with:
Fast implementation
Highly customizable
State-of-the-art technology
Intuitive interface
Mobile app
Align vendor risk with business goals
Highly secure
API integrations
More Resources Related to Vendor Risk Management Software

Using Automation to Build a Consolidated View of Third-Party Risk
This ebook explains how to build an effective third-party risk management program to get a holistic view of vendor risk…

3 Ways to Automate Third-party Risk Management
This blog explains how third-party risk management automation grants insight into vendor risk and automated processes.
The Complete Guide to Buying Risk Management Software
This ebook demystifies the software buying process, providing a step-by-step guide through the entire buying journey to help you identify the best vendor risk management software for your organization..
Find out more about Riskonnect’s vendor risk management software.
Learn more.
Frequently Asked Questions | Vendor Risk Management Software