PLATFORM SECURITY
Riskonnect solutions are built on a cloud-based platform with the highest end-to-end security
Total Access Control
Riskonnect offers the control needed to prevent unauthorized access to your data, down to the field level.
Global Data Centers
Data centers are located across the globe and are physically secured using a defense-in-depth approach.
Third-Party Certifications
Riskonnect’s best-in-class security has been independently certified.
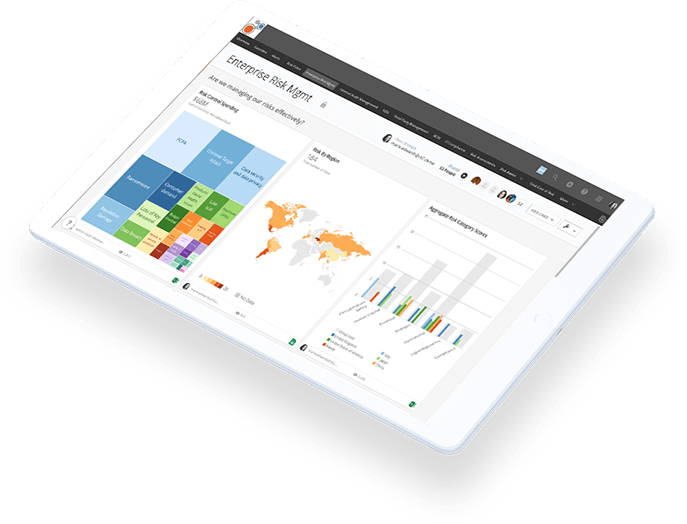
How’s Your View?
Find out how
Riskonnect can transform
the way you view risk.