As third-party related issues and breaches grow more frequent and costly, their overall impact on business operations and brand trust has become impossible to ignore. An alarming statistic in the Verizon 2025 Data Breach Investigations Report highlighted that 30% of data breaches involved a third party, up 15% from the previous year, making third-party risk management a top concern for CISOs.
RSAC ESAF CISOs Transforming Third-Party Risk Management
Although the modern technology offered by third-party vendors provides businesses with a wealth of capabilities to streamline and automate processes, each vendor becomes a new attack vector and exposes businesses to new risks.
Vendor technology issues often lead to operational failures, system downtime, compliance violations, data breaches, and reputational damage, impacting brand trust. In a bid to demonstrate resilience to the board, CISOs realize they can no longer manage third-party risk in isolation. Instead, they must manage it proactively, integrating it into their broader cybersecurity, GRC, and organisational resilience strategy.
Third-party vendors are an integral part of an organisation’s ecosystem, and any failure can cause catastrophic consequences. As vendors become part of the extended enterprise, firms expect them to uphold the same standards in business continuity planning, regulatory compliance, certifications, incident response, and risk management. Therefore, it is easy to see why organisations increasingly view third-party risk management not as an isolated discipline but as an extension of their existing processes.
When done well, third-party risk management can be used as a strategic advantage to empower organisations to embrace new technology and smarter working methods. Innovative CISOs can harness third-party risk management and use it as an enabler to move fast with AI, cloud technology solutions, and third-party integrations. Rather than blocking innovation to avoid risk, strong vendor risk practices should empower you to confidently engage promising new partners, with the proper onboarding, expectations, and controls in place.
Recent Reports Highlight Third-Party Risk as an Enterprise-Wide Concern
With such widespread use of third-party technologies, one might assume organisations would prioritize manageing their associated risks. But, in the latest Forrester report, The State of Third-Party Risk Management, 2024, only 8% of global risk management decision-makers selected third-party risk in their top 5 enterprise risk management concerns.
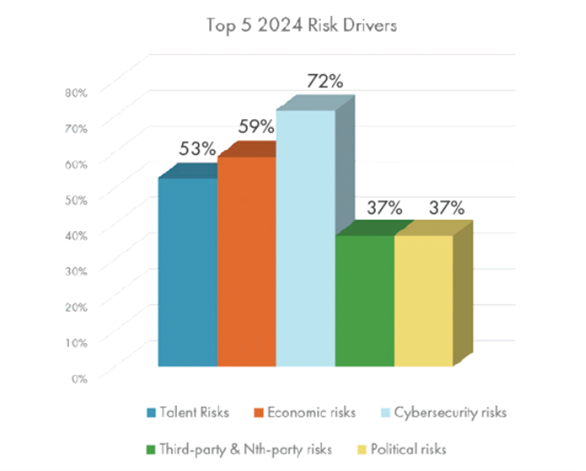
At first glance, the results suggest that organisations give limited attention to third-party risk. However, a closer look reveals that the top risks identified by risk leaders—such as data privacy, information security, emerging technology, regulatory compliance, business continuity, operational risk, and supply chain risk—are all inherently linked to third-party relationships. Therefore, rather than viewing third-party risk as a standalone category, the survey results suggest organisations recognize that third-party risk management must be embedded across their broader enterprise risk landscape and managed holistically. The recent results in The 2024 New Generation of Risk Report by Riskonnect found that 72% of companies surveyed considered cybersecurity to be a top risk driver in 2024, while 37% cited third-party and Nth party risks as a top priority, further highlighting the close links between third-party risk and cybersecurity.
Regulatory Pressure Brings an Increased Focus on Third-Party Risk Management
Third-party risk reliance is rising, and regulations are accelerating in line with this trend. With so many technology vendors flooding the market and AI solutions booming, it is no surprise that many widely adopted regulations touch on manageing the risks associated with service providers. ISO 27001, NIST, NIS2, COBIT, HIPAA, DORA, SEC, the GDPR, and APRA CPS 230 all include guidance on manageing third-party risk. Complying with regulations demands visibility and control, and a well-established third-party risk management programme supports businesses in demonstrating that their vendor network aligns with regulatory requirements.
CISO Accountability for Vendor-Related Incidents is Rising
As third-party risk management programmes have matured, organisations increasingly hold the CISO—not the contracting department—accountable for vendor-related incidents. This increased pressure and responsibility have seen third-party risk management programmes mature rapidly as CISOs implement additional checks and measures to safeguard the company and its reputation.
Here Are 6 Ways Proactive CISOs Turn Third-Party Risk Management into a Strategic Advantage
1. Tie Vendor Risk to Business Continuity and Incident Response Plans
Proactive CISOs understand that a breach, outage, or failure by a critical vendor can grind operations to a halt. Rather than treating vendor risk as a separate concern, smart CISOs integrate it directly into business continuity planning (BCP) and incident response playbooks. This approach helps ensure the organisation can continue operating during a vendor disruption—whether caused by cyberattacks, compliance failures, or operational breakdowns—and protects what matters most: avoiding costly business disruption and preserving brand trust. These outcomes resonate at the board level and help CISOs frame third-party risk as a core component of overall cyber resilience.
To integrate these processes successfully, your third-party risk management programme must:
- Map vendor services to business-critical functions
- Identify which third parties underpin core systems, processes, and regulatory obligations
This mapping enables you to understand the potential impact if a critical vendor fails and allows for risk-based prioritization of vendors in continuity planning.
In addition, organisations should also:
- Plan scenario and vulnerability testing exercises that include third-party failures to ensure preparedness extends to critical third-party vendors.
- Establish backup vendors and contingency plans.
- Ensure vendor assessments enquire about business continuity plans, incident response processes, and recovery time objectives to ensure their internal processes align with organisational expectations.
As the number of third-party vendors increases, so does the likelihood of vendor-related incidents and disruptions. To ensure timely and effective resolution, organisations must establish a clearly defined incident reporting process that captures third-party-related incidents, hazards, and near misses. These plans should include escalation protocols, communication plans, and remediation procedures.
2. Use Vendor Due Diligence to Drive Innovation and Digital Strategy
Whether it is AI, new markets, or digital rollouts, bold CISOs treat third-party risk as an input to innovation, rather than viewing it as an obstacle. In the Forrester report cited earlier, data shows that respondents who made the connection between increased levels of enterprise risk and increased reliance on third parties frequently describe risk management as an accelerator of innovation.
Strong third-party risk management enables CISOs to conduct due diligence quickly and confidently, allowing them to approve high-impact vendor partnerships without compromising security or compliance. This assurance is critical when adopting cutting-edge platforms or AI-powered tools.
To make fast, confident decisions, effective TPRM programmes focus on a few critical actions:
- Performing rapid risk assessments tailored to the vendor’s role and risk profile
- Leverageing AI and risk intelligence to flag issues relating to financial stability, compliance, or cybersecurity
- Ensuring clear expectations around SLAs, KPIs, and incident response
This strategic approach ensures that innovative vendors—especially smaller or more agile providers—can be onboarded without delay, ensuring they meet your thresholds for resilience and alignment with regulatory standards.
By embedding these controls early in the selection process, CISOs can move quickly without compromising the organisation’s risk appetite. Third-party risk management enables digital growth, empowering innovation teams to move faster with confidence.
3. Elevate Third-Party Risk to Provide Board-Level Visibility
CISOs should elevate third-party risk to the boardroom by framing it in terms of operational resilience, reputational risk, regulatory exposure, and financial consequences. CISOs who articulate vendor risk by highlighting business impact and long-term resilience get buy-in faster and safeguard trust with executive teams. There is also a risk in standing still. Boards must understand that avoiding new technology can create as much exposure as adopting it. This translation of risk data into meaningful metrics is essential for getting buy-in for new strategic vendors and gaining executive support for stronger third-party risk management programmes, ongoing investment, and cross-functional engagement.
When done well, third-party risk management becomes a powerful leadership tool that helps CISOs move quickly and get approvals to implement new technology, enabling their organisations to stay ahead of the curve in an increasingly competitive market. CISOs who regularly raise vendor risk in board meetings and present meaningful metrics are more likely to secure resources and influence vendor selection decisions, helping their companies adopt new digital solutions that advance the business model.
Board-level visibility of third and fourth-party risks limits surprises when incidents occur. Successful third-party risk management programmes ensure leadership teams are already aligned on response protocols, escalation procedures, and the potential impact of a failed vendor, minimizing panic when vendor-related incidents do occur.
4. Connect the Dots Across Teams and Tools
Less mature organisations often store third-party risk data across disparate systems and data sources. Different teams and departments onboard vendors without any central point of oversight, and the vetting process lacks consistency. In other cases, procurement has contracts, IT owns access management, compliance tracks certifications, and risk teams manage assessments. In a fragmented environment, teams often miss due diligence steps, overlook critical warning signs, and deliver disjointed response efforts. Disconnected data and tools limit visibility, impairing timely risk detection. This lack of oversight makes prioritizing mitigation or reporting accurately to the board harder for CISOs and directly impacts their ability to lead strategically.
Proactive CISOs recognize that this approach lacks consistency and oversight and use third-party oversight to break down walls. They centralize vendor data in shared platforms or dashboards and implement consistent processes for onboarding, conducting risk assessments, benchmarking, scorecarding, and performing due diligence checks to avoid missing risk signals.
This unified approach ensures a fair evaluation of vendors through cross-functional governance structures that automate data sharing between systems. It gives risk leaders a holistic view of vendor risk and dependencies, empowering them to prioritize mitigating the most critical risks and keep the board informed.
Standardizing your risk framework, assessment templates, due diligence processes, onboarding, and offboarding makes vendors more comparable, making it easy to detect poorly performing, high-risk vendors. Access to interconnected third-party risk management data enables the board to make faster, more informed decisions when choosing new vendors and technology partners.
According to OCEG, “CISOs are no longer just technical experts. They are boardroom voices guiding business strategy, and the GRC function is evolving right along with them”. CISOs must work with GRC teams to harness the correct data to advise the board on the best action to protect the organisation from cyber and third-party risk.
5. Shift From Static Assessments to Continuous Monitoring
The strongest third-party risk management programmes incorporate real-time, continuous monitoring of vendors and their performance and consider their impact on critical services. A recent OCEG article stated that “Real-time risk intelligence is now expected. Whether it’s continuous control monitoring, real-time vendor scoring, or predictive alerts about regulatory changes, organisations are expected to know that their risk controls are effective”.
Initial assessments during onboarding and annual reviews are no longer sufficient to stay ahead of third-party risks. SecurityScorecard’s 2023 breach researchstates that at least 29% of all breaches involved third-party attack vectors. Vendor risk evolves fast, and CISOs need near real-time visibility and continuous monitoring to stay ahead of emerging threats.
CISOs at the forefront use real-time data to track changes in vendor performance. They subscribe to third-party risk intelligence providers to understand if suppliers are hitting the headlines because of financial instability, compliance violations, and ethical mishaps. They also perform regular risk assessments and conduct questionnaires on a monthly or quarterly basis to detect changes in circumstances that could pose a risk. Vendor-reliant processes can also be factored into regular business continuity plan updates and scenario and vulnerability testing, ensuring adequate contingency planning.
This continuous monitoring allows organisations to be more agile and proactive instead of waiting for a yearly review or a crisis before re-evaluating a vendor! With ongoing monitoring, regular assessments, and due diligence, CISOs can identify early warning signals and take preventive action. This integrated best-practice approach also supports more accurate risk scoring based on how each vendor connects to critical services, rather than treating all vendors equally. This ongoing stream of data relating to vendors and their performance enables businesses to make dynamic, responsive decisions on their choice of vendors and act quickly to avert vendor-related crises.
6. Leverage AI
AI is accelerating rapidly, and today’s CISOs must look beyond the hype to harness AI’s real, practical value, particularly in manageing third-party risk. By embedding AI into their processes, CISOs can eliminate manual, repetitive tasks, surface insights faster, and respond to emerging threats with greater agility. AI is critical in third-party risk management, where manually assessing hundreds – or even thousands – of vendors is no longer sustainable.
AI can streamline onboarding, automate due diligence checks, flag anomalies in vendor behaviour, and even predict future risk based on historical patterns and external data. It enables CISOs to scale their oversight without increasing headcount and to move from reactive assessments to proactive risk intelligence.
OCEG says, “Generative and agentic AI can already auto-populate risk assessments, detect control redundancies, scan regulations, and even summarize weekly risk reports into executive insights. But while AI promises big gains in productivity, it also introduces new risks: hallucinations, bias, data privacy violations, and unclear ownership.”
Because AI brings big opportunities and serious risks, smart CISOs should lead the conversation, not watch from the sidelines. Those who embrace AI responsibly, with strong governance and controls, will position their organisations to mitigate third-party risk more effectively and gain a competitive edge. AI is not just another tool, but a strategic advantage for those who use it wisely.
Third-Party Risk Management as a Driver for Strategic Advantage
In an increasingly digital and interconnected business landscape, third-party risk management is not just there to prevent operational and compliance issues; it is a strategic business enabler. Proactive CISOs recognize that third-party vendors broaden the attack surface and manage them with the same rigor as internal processes. By embedding third-party risk management and AI into core areas like business continuity, digital transformation, executive decision-making, and daily risk management activities, CISOs turn vendor risk management into a vital source of intelligence that enables their organisations to adopt modern technology at pace.
The most forward-thinking CISOs are no longer content with reactive or disjointed approaches. They are shifting toward integrated, strategic supplier risk management programmes that reduce risk and unlock opportunities to innovate and grow. The rigorous continuous monitoring and vetting in today’s third-party risk management programmes and the increased use of AI provide vital data to support decision-making, enabling a pre-emptive approach that addresses vendor risk before it becomes problematic.
Manageing third-party risk holistically drives resilience, agility, and long-term competitive advantage. CISOs must move from a mindset of risk avoidance to one of confident, risk-informed innovation by using third-party risk data to identify issues and dependencies in their vendor ecosystem, ensuring their organisations are poised to adopt new technology and service providers confidently.
Want to go deeper? Explore this ebook on third-party risk management to see how organisations are evolving their programmes to meet today’s challenges, or contact Riskonnect for a demo of our third-party risk platform.




